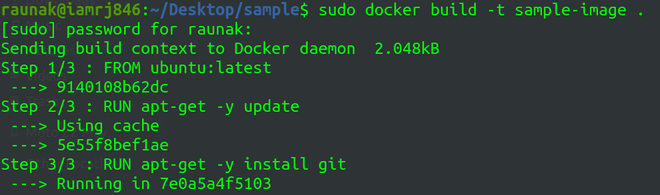
Version control is one of the most important aspects of any software development project, and when we talk about version control, there is no better tool than Git. Most developers rely on Git to manage and share their project components among team members. Even if you’re running your project on Docker, you’ll still be able to…
JavaScript is the programming language of the web, which makes it very important! However, in contrast to R and Python, it is primarily used as a scripting language in web development and has little to do with machine learning or data science. This is because R and Python are particularly well-suited for data science or machine learning, with a…
Router: A router is a networked device that forwards data packets between computer networks. The device is usually connected to two or more different networks. When a packet arrives at a router port, the router will read the address information from the packet to determine which port the packet will be sent to. For example, a router…
The separator between the arguments of the print() function in Python is a space by default (a software space feature), it can be modified, and it can be set to any character, integer or string according to our choice. The “sep” parameter is used to implement the same functionality and is only found in python 3.x or later. It is…
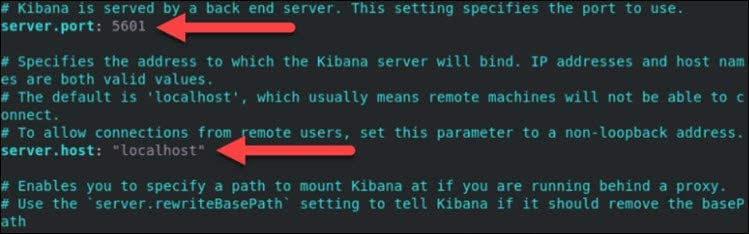
Introduce How Do I Configure Nginx Reverse Proxy in Kibana? The easiest way to protect your Kibana dashboard from malicious intruders is to set up an Nginx reverse proxy. By doing so, you can ensure that only password-protected, authorized users can access Kibana (and the data in Elasticsearch). How Do I Configure Nginx Reverse Proxy…
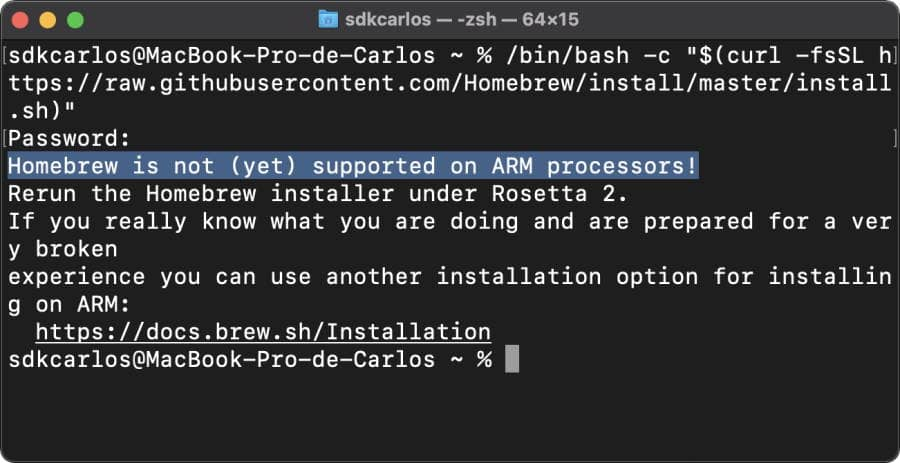
Learn how to fix problems installing Homebrew on a MacBook with an M1 chip. After trying to install Homebrew on a new MacBook Pro 13″ 2020, the above error exception appears on the terminal. In this article, I will explain to you how to fix this issue and continue with the workflow as usual. Install…
With the advent of industrial tools for penetration testing and bug bounty search, the field of ethical hacking is facing tremendous growth. When learning about ethical hacking in technology, in addition to mastering outdated vulnerabilities and lab attacks, you should also understand their basic tools. If you’re not already familiar with ethical hacking, let’s define the technology before…
If 2 numbers have the same frequency, the elements of the array are printed at a decreasing frequency, and then the frequency at which the first one occurs. Example: We have discussed the different approaches in the following posts: Sort elements by frequency|S1 Sort elements by frequency|S2 Sort array elements by frequency S3 (using STL)…
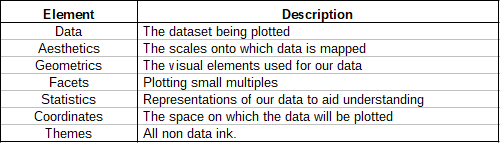
ggplot2 is also known as graph syntax, and it is a free, open-source, easy-to-use visualization package that is widely used in R. It is the most powerful visualization package written by Hadley Wickham. It includes several layers to manage it. The layers are as follows: The building blocks of a layer The layers with variables…
SAP Labs visited our campus on September 30th to recruit final students for associate developer roles, and they allow EE and MCA, MSc, and all CSE M.Tech students from CSE, IT, ECE, and B.Tech to participate in the recruitment event. Conditions: CPI ≥7, 10th and 12th both reach 60% Dispose: On October 1st, the PowerPoint and online test…