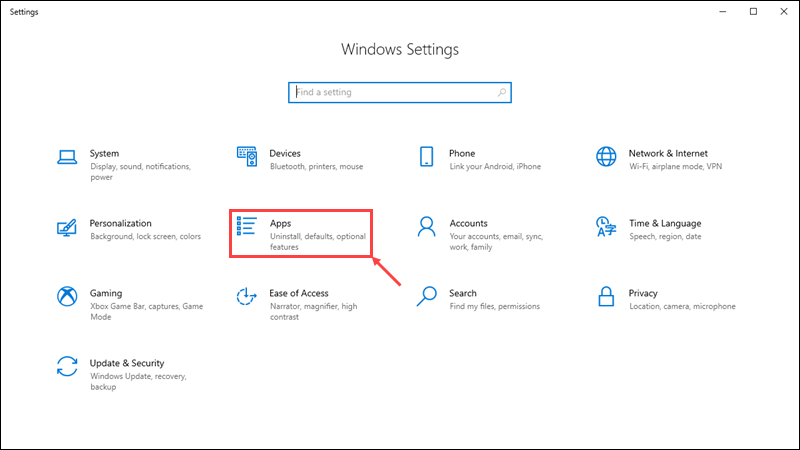
Windows Hyper-V installation Ubuntu tutorial is introduced How to install Ubuntu on Windows with Hyper-V? Since the launch of the Windows 10 Fall Creators Update, it has been possible to run Ubuntu natively on Windows 10. However, there are some limitations to running Ubuntu natively on Windows, such as being limited to using the command-line…
Tutorial on installing and using Flask Flask is one of the most popular web application frameworks written in Python. It is a micro-framework designed for a simple and quick start-up. Scaling with tools and libraries adds more functionality to Flask for more complex projects. How does Flask install and use? This article explains how to install…
std::is_destructible template C++ STL exists in <type_traits> header file. The std::is_destructibleC++ STL template is used to check if it is destructible. One class is called destructible, and its destructor is not removed and may be accessible in the derived class. A boolean value is returned true if the following conditions are met: T is a destructible…
Serverless architectures are an alternative to high-maintenance, resource-wasting servers. With serverless deployments, you only pay for what you use. It saves you from having to deal with multiple server setups and their configurations. So it’s no surprise that today’s developers flock to serverless applications. With AWS Lambda and serverless frameworks, you can quickly deploy scalable…
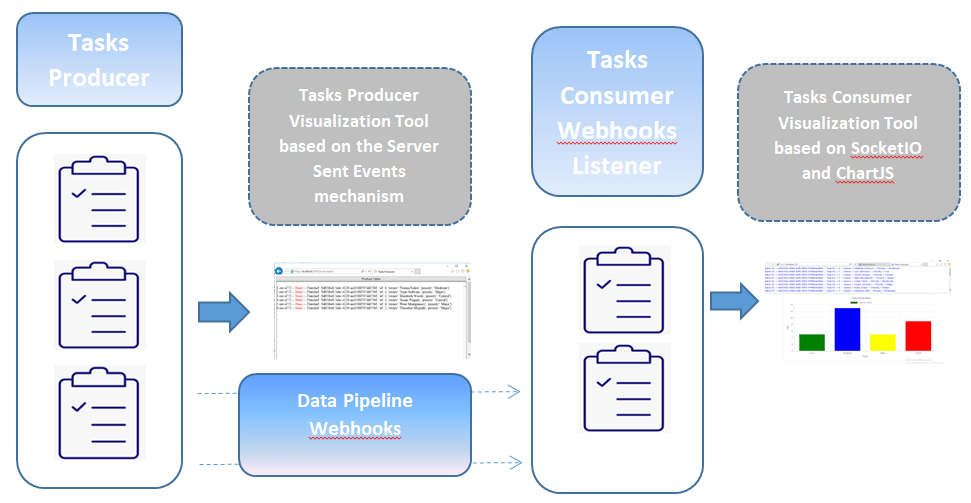
How Python Flask uses webhooks: Learn how to create streaming applications with real-time charts by using webhooks with the help of Flask, Redis, SocketIO, and other libraries in Python, including some examples of webhook usage. Introduction to the tutorial on how to use webhooks Webhooks can be thought of as an API that is driven by events…
What are the applications of data science in e-commerce? One good thing is the advent of e-commerce sites thanks to the internet. Now you can sit at home and order anything you want, and it will be delivered to your doorstep! Want a new phone? Order online! Looking for new shoes? Just enter your size and you’re…
One of the advantages of C++ over C is exception handling. An exception is a runtime exception or anomaly that a program encounters during its execution. There are two types of exceptions: a) synchronous and b) asynchronous (e.g. out of the program’s control, disc failure, etc.). To this end, C++ provides the following specialized keywords. try:…
Learning programming online is no longer a novelty, and it doesn’t even require special courses or skills among hobbyists. Moreover, coding is not limited to IT professionals or industries that use it regularly, but also includes various artists, designers, creative business professionals, etc., for fun and to gain new skills. If you’re also new to…
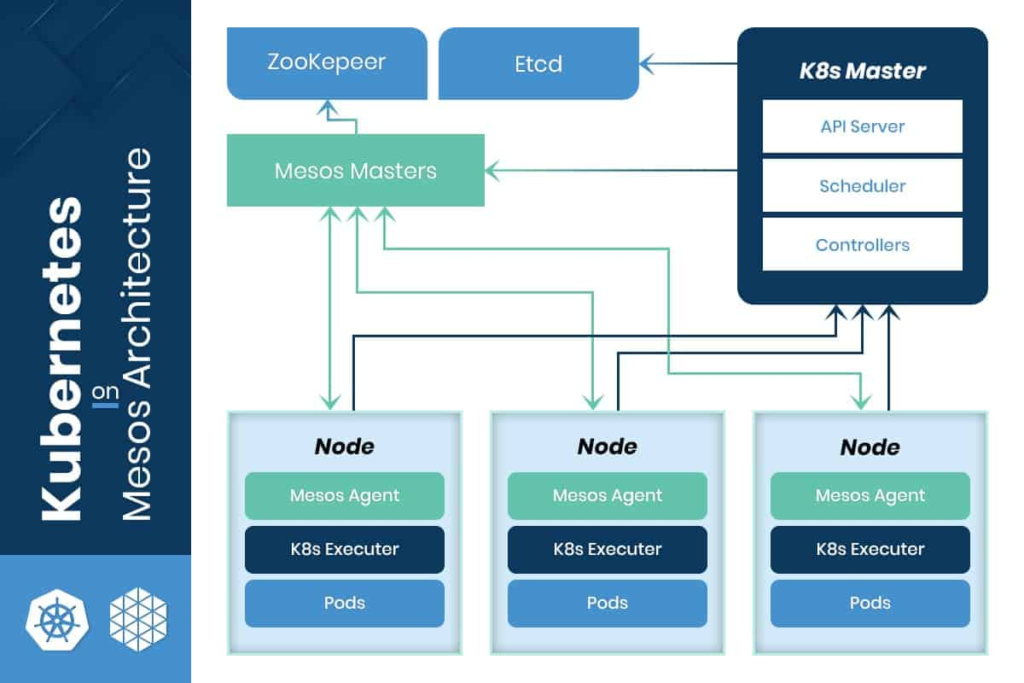
Container orchestration is a fast-growing technology. There are currently 3 industry giants; Kubernetes, Docker Swarm, and Apache Mesos. They fall into the category of DevOps infrastructure management tools called “container orchestration engines.” Docker Swarm has won the hearts of customers and has become the first choice for containerization. Kubernetes and Mesos are the main competitors. What…
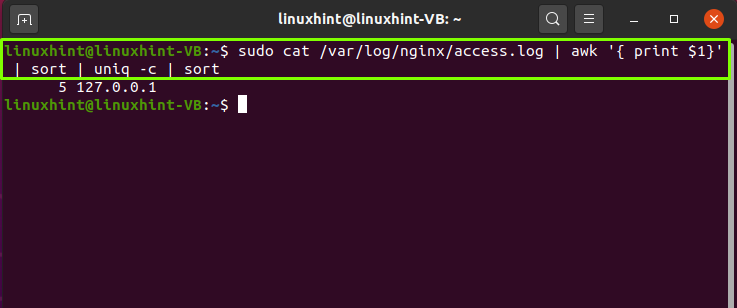
If you want to optimize your web server, it is essential to understand Nginx access logs and learn how to handle nginx access logs. Logging is the single critical action you take before you run into a problem. It also plays a role in detecting flaws in web development. Nginx access logs contain detailed information about user access requests. How…