Do you want to know what are the most important steps you can take to protect against ransomware? How can I protect my server from ransomware? Here’s how to protect your server from ransomware. Cybercrime is on the rise, and hackers are looking for sophisticated ways to infect networks with malware every day as time goes…
Choosing the right security information and event management software can be overwhelming, but what are the open source SIEM tools? This article is a complete ranking of SIEM open source tools. Today’s SIEM market is a nearly $3 billion industry and growing. Gartner predicts that spending on SIEM technology will grow to nearly $3.4 billion by 2021. When considering…
This article creates a fake access point and tricks nearby devices by using scapy in python to send a valid beacon frame into the air, including a Python example of creating a fake access point. How does Python create fake access points? Ever wondered how your laptop or phone knows what wireless networks are nearby? It’s…
Content Summary – Do you see CefSharp.BrowserSubprocess.exe named processes running on your computer? Didn’t you notice it before? Could it be a virus? Read the blog to find out what it is and how to fix it. CefSharp.BrowserSubprocess.exe Tips & Guides: Did you happen to witness a strange-looking process CefSharp.BrowserSubprocess.exe running on TaskManager on your PC?…
How to check your website for SQL injection vulnerabilities: This article describes how to use the SQLMAP penetration testing tool to test whether a website can avoid SQL injection. SQLMAP Testing SQL Injection Vulnerability: What is SQL Injection? SQL injection is a code injection technique where an attacker can execute a malicious SQL query that…
As the word suggests, hacking has nothing to do with any morality. Hacking is the attempt to force access to someone’s system with a fraudulent mindset in order to compromise his privacy or steal his system data. Still, if weaknesses and threats to a computer network or individual unit are identified with implicit and approved…
Windows systems seem to face endless security issues, and online villains are something that experts can exploit. Despite having a strong and effective built-in firewall, Windows PCs need to be protected from online threats in addition to blocking viruses, trojans, rootkits, and hackers from infiltrating the system. What are the commonly used firewall software downloads…
How to install and set up Fail2Ban? Fail2ban is a software that protects your server from brute force attacks. It does this by monitoring server logs and detecting any suspicious activity. The program detects when there is an unreasonable number of failed attempts and automatically adds new additions to Block iptables for a given IP. This IP…
The crypt32.dll module is responsible for executing several Cryptographic Messaging and Certificate functions in the Crypto API, but different versions of the program have different capabilities. The primary purpose of the Crypto API is to serve developers of Windows-based applications to allow their users to generate and trade documents and data in a secure and protected environment. Crypt32.dll as…
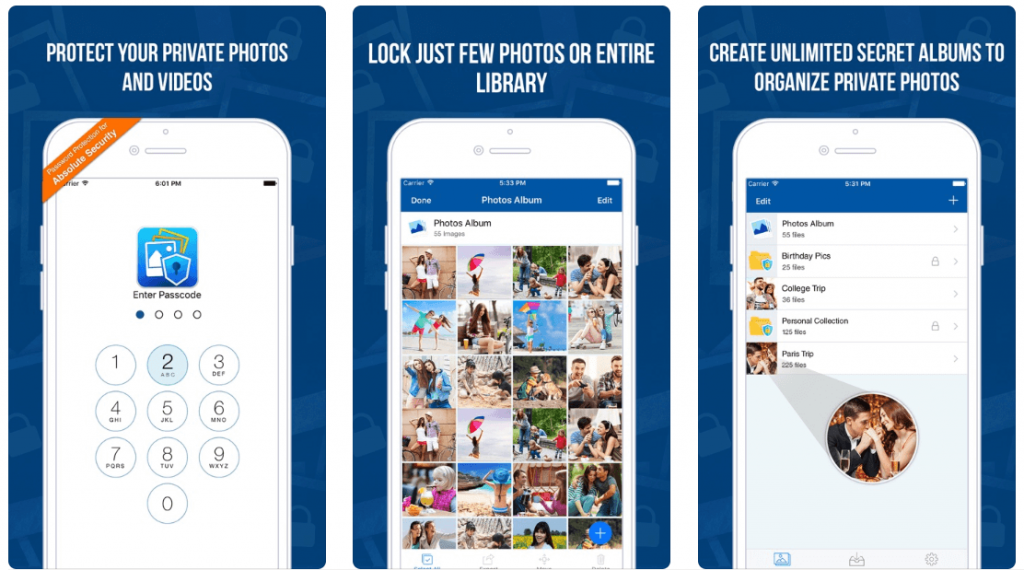
Everyone clicks on the picture to keep their memory permanent. However, keeping your private photos safe is a concern because they are not safe in your albums. When you give your iPhone to someone else to view any picture in the Photos app, you have two options: either delete your private photos or let the…