How to install and set up Fail2Ban? Fail2ban is a software that protects your server from brute force attacks. It does this by monitoring server logs and detecting any suspicious activity.
The program detects when there is an unreasonable number of failed attempts and automatically adds new additions to Block iptables for a given IP. This IP (or host) will then be blocked for a specified time or indefinitely.
Therefore, installing this log monitoring software is an excellent way to provide another layer of protection to your server security. Still, it can only be part of your overall server security plan. Explore more with these 21 server security tips.
In this tutorial, you’ll learn how to install and configure Fail2ban on your server.
Prerequisite
- Access the Command Line / Terminal window
- Access user accounts with sudo or root privileges
Install Fail2ban
Fail2Ban Installation and Setup Guide: How you install Fail2ban depends on the operating system running on your server. Below you will find commands to install and enable Fail2ban on Ubuntu, CentOS, Fedora, and Debian.
Important: Fail2ban is not a replacement for software firewalls, such as iptables. It is intended to serve as another layer of security and should not be a substitute for a firewall.
Fail2Ban Installation and Setup Tutorial: Install Fail2ban on Ubuntu
1. It is important to update the system repository and upgrade the software before adding a new package. To do this, run the following command:
apt-get update && apt-get upgradePress y to confirm and press Enter.
2. Now you can install Fail2ban with the following command:
apt-get install fail2ban3. Alternatively, you can install Sendmail to support email:
apt-get install sendmail4. Next, you need to allow SSH access through the firewall:
ufw allow ssh5. Finally, enable the firewall:
ufw enableHow to install and set up Fail2Ban: Install Fail2ban on CentOS
1. To install Fail2ban on CentOS, you need the EPEL repository. Update the system and add repositories by running the following command:
yum update && yum install epel-release2. Once the EPEL repository is set up, install Fail2ban using the following command:
yum install fail2ban3. Next, you need to start the Fail2ban service and enable it on startup:
systemctl start fail2bansystemctl enable fail2ban4. For email support, you can install Sendmail by:
yum install sendmail5. To start and enable the Sendmail service, run:
systemctl start sendmailsystemctl enable sendmailInstall Fail2ban on Fedora
1. Start by updating the system :
dnf update2. Then, install Fail2ban and Sendmail (optionally if you need email support):
dnf install fail2bandnf install sendmail3. Since these services don’t start automatically on Fedora, you’ll need to start and enable them using the following command:
systemctl start fail2bansystemctl enable fail2bansystemctl start sendmailsystemctl enable sendmailFail2Ban Installation and Setup Tutorial: Install Fail2ban on Debian
1. Update and upgrade the system:
apt-get update && apt-get upgrade -yPress y and Enter to confirm.
2.Then, install Fail2ban using the following command:
apt-get install fail2ban3. For email support, you can also install Sendmail with the following command:
apt-get install sendmail-bin sendmailFail2Ban Installation and Setup Guide: Configure Fail2ban
Configure Fail2ban by editing the following configuration file:
- fail2ban.local file
- jail.local file
Configure the fail2ban.local file
How to install and set up Fail2Ban? Fail2ban defines its global configuration in the fail2ban.conf file. This file consists of a default configuration and is generally not recommended to be modified.
All changes to the configuration should be done in a separate fail2ban.local file.
1. Therefore, the first thing to do is to copy the contents of the .conf file into the .local file. The command to do so is:
cp /etc/fail2ban/fail2ban.conf /etc/fail2ban/fail2ban.local2. There will be no output after this command. The next step is to open the fail2ban.local file with a text editor of your choice:
nano fail2ban.local3. You should see a file similar to the image below:

In this example, the blue annotation explains each option and its possible value. The white lines are options that you can modify, and they include:
loglevel– Sets the log level output , , , , , or .CRITICAL,ERRORWARNINGNOTICEINFODEBUGlogtarget– Set the target of the log, which can beFILE,SYSLOG,STDERR, orSTDOUT.syslogsocket– Set the syslog socket file toeither autoorFILE(This only uses SYSLOG whenlogtargetis set to)socket– Sets the socket file used to communicate with the daemon. Make sure you don’t delete this file. Its default path is:/var/run/fail2ban/fail2ban.sockpidfile– Set up a PID file to store the fail2ban server process ID. The default location is:/var/run/fail2ban/fail2ban.pid
Configure the jail.local file
Fail2Ban Installation and Setup Guide: Another Fail2ban configuration file you may need to modify is the jail.conf file, which contains the prison that defines a filter with an action.
Just like the global configuration, the jail.config file should not be modified directly. Instead, all customizations should be made in the jail.local file.
1. If you do need to make some changes, copy the contents of the .conf file into the .local file:
cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local2. Open the jail.local file with a text editor of your choice:
nano jail.local3. You should see the following:
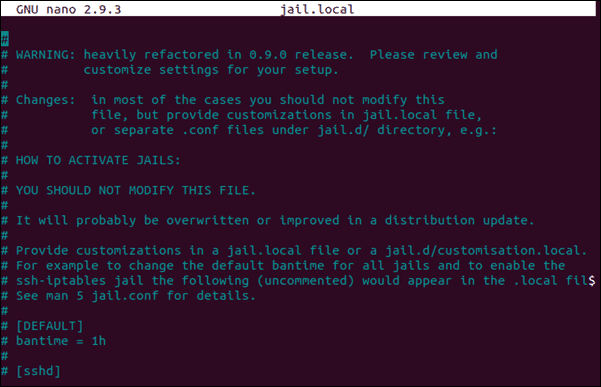
You can set the following options there:
ignoreself– Specify whether local IP addresses should be ignored by setting a value (default) or .truefalseignoreip– Allows you to specify IP addresses, CIDR masks, or DNS hosts that should be banned. Separate multiple addresses with a space.ignorecommand– Defines whetherpath/to/commandshould be ignored or not.
bantime– Specifies the number of seconds the host is banned (defaults to 600)maxretry– The number of failures allowed before the host is banned (the default setting is5).findtime– The amount of time that the host should not run out ofmaxretrynumbers to avoid being banned (usuallyset to 10minutes). For example, if a host fails 5 times in 10 minutes, it will be banned for 600 seconds.
backend– Specifies the backend used to get file modifications. If you’re using CentOS or Fedora, you’ll need to set your backend tosystemd.autofor other operating systems, the default value is sufficient.[ssh]– By default, Fail2ban does not have jails enabled. Therefore, you need to do this manually by adding jails to the configuration file. For example, you can do this by uncommenting (removing#) the line[ssh]andenabled = true.
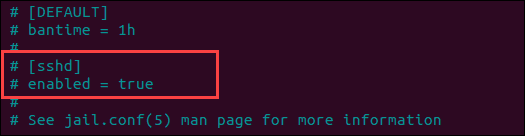
destemail– Specify the email address you want to receive notifications fromsender– Defines the email address to receive notifications
Additional jail.local configuration
How to install and set up Fail2Ban? You can also set other configurations, such as SSH and iptables, in the jail.local file. These options include:
banaction– specifies the default action to use whenmaxretryarrives.banaction_allports– Allows you to flag IPs that should be blocked in each port.port– This value should correspond to the service that is set. This could bean SSHor a port number if you’re using an alternate port.filter– The name of the file containing the failregex information, located at/etc/fail2ban/filter.d.
Restart the service
If you make any changes to the fail2ban.local and jail.local files, make sure to restart the fail2ban service.
To restart the fail2ban service with the new configuration, run the following command:
service fail2ban restartFail2Ban Installation and Setup Tutorial Conclusion
By following this Fail2Ban installation and setup guide, you should already be able to install and set up the basic configuration of Fail2ban.
Fail2ban is a great tool for adding another layer of security. It is particularly effective against SSH brute force attacks.